7. Internal Models Method for Counterparty Credit Risk
Approval to Adopt an Internal Models Method to Estimate EAD
7.1. A bank that wishes to adopt an internal models method to measure exposure or exposure at default (EAD) for regulatory capital purposes must seek SAMA approval. The internal models method is available both for banks that adopt the internal ratings-based approach to credit risk and for banks for which the standardized approach to credit risk applies to all of their credit risk exposures. The bank must meet all of the requirements given in 7.6 to 7.60 and must apply the method to all of its exposures that are subject to counterparty credit risk, except for long settlement transactions.
7.2. A bank may also choose to adopt an internal models method to measure counterparty credit risk (CCR) for regulatory capital purposes for its exposures or EAD to only over-the-counter (OTC) derivatives, to only securities financing transactions (SFTs), or to both, subject to the appropriate recognition of netting specified in 7.61 to 7.71. The bank must apply the method to all relevant exposures within that category, except for those that are immaterial in size and risk. During the initial implementation of the internal models method, a bank may use the Standardized Approach for counterparty credit risk for a portion of its business. The bank must submit a plan to SAMA to bring all material exposures for that category of transactions under the internal models method.
7.3. For all OTC derivative transactions and for all long settlement transactions for which a bank has not received approval from SAMA to use the internal models method, the bank must use the standardized approach to counterparty credit risk (SA-CCR, in Chapter 6 of this framework).
7.4. Exposures or EAD arising from long settlement transactions can be determined using either of the methods identified in this framework regardless of the methods chosen for treating OTC derivatives and SFTs. In computing capital requirements for long settlement transactions banks that hold permission to use the internal ratings-based approach may opt to apply the risk weights under this Framework’s standardized approach for credit risk on a permanent basis and irrespective to the materiality of such positions.
7.5. After adoption of the internal models method, the bank must comply with the above requirements on a permanent basis. Only under exceptional circumstances or for immaterial exposures can a bank revert to the standardized approach for counterparty credit risk for all or part of its exposure. The bank must demonstrate that reversion to a less sophisticated method does not lead to an arbitrage of the regulatory capital rules.
Exposure Amount or EAD Under the Internal Models Method
7.6. CCR exposure or EAD is measured at the level of the netting set as defined in Chapter 4 of this framework and 7.61 to 7.71 of this framework. A qualifying internal model for measuring counterparty credit exposure must specify the forecasting distribution for changes in the market value of the netting set attributable to changes in market variables, such as interest rates, foreign exchange rates, etc. The model then computes the bank’s CCR exposure for the netting set at each future date given the changes in the market variables. For margined counterparties, the model may also capture future collateral movements. Banks may include eligible financial collateral as defined in 9.37 of the Minimum Capital Requirements for Credit Risk and 9.2 of this framework in their forecasting distributions for changes in the market value of the netting set, if the quantitative, qualitative and data requirements for internal models method are met for the collateral.
7.7. Banks that use the internal models method must calculate credit RWA as the higher of two amounts, one based on current parameter estimates and one based on stressed parameter estimates. Specifically, to determine the default risk capital requirement for counterparty credit risk, banks must use the greater of the portfolio-level capital requirement (not including the credit valuation adjustment, or CVA, charge in Chapter 11 of this Framework) based on Effective expected positive exposure (EPE) using current market data and the portfolio level capital requirement based on Effective EPE using a stress calibration.24 The stress calibration should be a single consistent stress calibration for the whole portfolio of counterparties. The greater of Effective EPE using current market data and the stress calibration should not be applied on a counterparty by counterparty basis, but on a total portfolio level.
7.8. To the extent that a bank recognizes collateral in EAD via current exposure, a bank would not be permitted to recognize the benefits in its estimates of loss given-default (LGD). As a result, the bank would be required to use an LGD of an otherwise similar uncollateralized facility. In other words, the bank would be required to use an LGD that does not include collateral that is already included in EAD.
7.9. Under the internal models method, the bank need not employ a single model. Although the following text describes an internal model as a simulation model, no particular form of model is required. Analytical models are acceptable so long as they are subject to supervisory review, meet all of the requirements set forth in this section and are applied to all material exposures subject to a CCR-related capital requirement as noted above, with the exception of long settlement transactions, which are treated separately, and with the exception of those exposures that are immaterial in size and risk.
7.10. Expected exposure or peak exposure measures should be calculated based on a distribution of exposures that accounts for the possible non-normality of the distribution of exposures, including the existence of leptokurtosis (“fat tails”), where appropriate.
7.11. When using an internal model, exposure amount or EAD is calculated as the product of alpha times Effective EPE, as specified below (except for counterparties that have been identified as having explicit specific wrong way risk – see 7.48):
EAD = α × EffectiveEPE (Equation 1)
7.12. Effective EPE is computed by estimating expected exposure (EEt) as the average t exposure at future date t, where the average is taken across possible future values of relevant market risk factors, such as interest rates, foreign exchange rates, etc. The internal model estimates EE at a series of future dates t1, t2, t3 ...25 Specifically, “Effective EE” is computed recursively using the following formula, where the current date is denoted as t0 and Effective EEt0 equals current exposure:
EffectiveEEtk = max(EffectiveEEtk-1, EEtk (Equation 2)
7.13. In this regard, “Effective EPE” is the average Effective EE during the first year of future exposure. If all contracts in the netting set mature before one year, EPE is the average of expected exposure until all contracts in the netting set mature. Effective EPE is computed as a weighted average of Effective EE, using the following formula where the weights Δtk= tk - tk-1 allows for the case when future exposure is calculated at dates that are not equally spaced over time:

7.14. Alpha (α) is set equal to 1.4.
7.15. SAMA may require a higher alpha based on a bank’s CCR exposures. Factors that may require a higher alpha include the low granularity of counterparties; particularly high exposures to general wrong-way risk; particularly high correlation of market values across counterparties; and other institution specific characteristics of CCR exposures.
Own estimates for alpha
7.16. Banks should seek approval from SAMA to compute internal estimates of alpha subject to a floor of 1.2, where alpha equals the ratio of economic capital from a full simulation of counterparty exposure across counterparties (numerator) and economic capital based on EPE (denominator), assuming they meet certain operating requirements. Eligible banks must meet all the operating requirements for internal estimates of EPE and must demonstrate that their internal estimates of alpha capture in the numerator the material sources of stochastic dependency of distributions of market values of transactions or of portfolios of transactions across counterparties (e.g. the correlation of defaults across counterparties and between market risk and default).
7.17. In the denominator, EPE must be used as if it were a fixed outstanding loan amount.
7.18. To this end, banks must ensure that the numerator and denominator of alpha are computed in a consistent fashion with respect to the modelling methodology, parameter specifications and portfolio composition. The approach used must be based on the bank's internal economic capital approach, be well-documented and be subject to independent validation. In addition, banks must review their estimates on at least a quarterly basis, and more frequently when the composition of the portfolio varies over time. Banks must assess the model risk and inform SAMA of any significant variation in estimates of alpha that arises from the possibility for mis-specification in the models used for the numerator, especially where convexity is present.
7.19. Where appropriate, volatilities and correlations of market risk factors used in the joint simulation of market and credit risk should be conditioned on the credit risk factor to reflect potential increases in volatility or correlation in an economic downturn. Internal estimates of alpha should take account of the granularity of exposures.
24 Effective expected positive exposure (EPE) using current market data to be compared with Effective EPE using a stress calibration on annual basis during ICAAP
25 In theory, the expectations should be taken with respect to the actual probability distribution of future exposure and not the risk-neutral one. Supervisors recognize that practical considerations may make it more feasible to use the risk-neutral one. As a result, supervisors will not mandate which kind of forecasting distribution to employ.Maturity
7.20. If the original maturity of the longest-dated contract contained in the set is greater than one year, the formula for effective maturity (M) in 12.42 of the Minimum Capital Requirements for Credit Risk is replaced with formula that follows, where dfK is the risk-free discount factor for future time period tK and the remaining symbols are defined above. Similar to the treatment under corporate exposures, M has a cap of five years.26
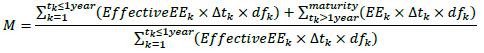
7.21. For netting sets in which all contracts have an original maturity of less than one year, the formula for effective maturity (M) i in 12.42 of the Minimum Capital Requirements for Credit Risk is unchanged and a floor of one year applies, with the exception of short-term exposures as described in paragraphs in 12.45 to 12.48 of the Minimum Capital Requirements for Credit Risk.
26 Conceptually, M equals the effective credit duration of the counterparty exposure. A bank that uses an internal model to calculate a one-sided credit valuation adjustment (CVA) can use the effective credit duration estimated by such a model in place of the above formula with prior approval of SAMA.
Margin Agreements
7.22. If the netting set is subject to a margin agreement and the internal model captures the effects of margining when estimating EE, the model's EE measure may be used directly in (Equation 2) in 7.12. Such models are noticeably more complicated than models of EPE for unmargined counterparties.
7.23. An EPE model must also include transaction-specific information in order to capture the effects of margining. It must take into account both the current amount of margin and margin that would be passed between counterparties in the future. Such a model must account for the nature of margin agreements (unilateral or bilateral), the frequency of margin calls, the margin period of risk, the thresholds of unmargined exposure the bank is willing to accept, and the minimum transfer amount. Such a model must either model the mark-to-market change in the value of collateral posted or apply this Framework's rules for collateral.
7.24. For transactions subject to daily re-margining and mark-to-market valuation, a supervisory floor of five business days for netting sets consisting only of repo style transactions, and 10 business days for all other netting sets is imposed on the margin period of risk used for the purpose of modelling EAD with margin agreements. In the following cases a higher supervisory floor is imposed:
(1) For all netting sets where the number of trades exceeds 5000 at any point during a quarter, a supervisory floor of 20 business days is imposed for the margin period of risk for the following quarter.
(2) For netting sets containing one or more trades involving either illiquid collateral, or an OTC derivative that cannot be easily replaced, a supervisory floor of 20 business days is imposed for the margin period of risk. For these purposes, "Illiquid collateral" and "OTC derivatives that cannot be easily replaced" must be determined in the context of stressed market conditions and will be characterized by the absence of continuously active markets where a counterparty would, within two or fewer days, obtain multiple price quotations that would not move the market or represent a price reflecting a market discount (in the case of collateral) or premium (in the case of an OTC derivative). Examples of situations where trades are deemed illiquid for this purpose include, but are not limited to, trades that are not marked daily and trades that are subject to specific accounting treatment for valuation purposes (e.g. OTC derivatives or repo-style transactions referencing securities whose fair value is determined by models with inputs that are not observed in the market).
(3) In addition, a bank must consider whether trades or securities it holds as collateral are concentrated in a particular counterparty and if that counterparty exited the market precipitously whether the bank would be able to replace its trades.
7.25. If a bank has experienced more than two margin call disputes on a particular netting set over the previous two quarters that have lasted longer than the applicable margin period of risk (before consideration of this provision), then the bank must reflect this history appropriately by using a margin period of risk that is at least double the supervisory floor for that netting set for the subsequent two quarters.
7.26. For re-margining with a periodicity of N-days the margin period of risk should be at least equal to the supervisory floor, F, plus the N days minus one day. That is:
Margin Period of Risk = F + N — 1
7.27. Banks using the internal models method must not capture the effect of a reduction of EAD due to any clause in a collateral agreement that requires receipt of collateral when counterparty credit quality deteriorates.
Model validation
7.28. The extent to which banks meet the qualitative criteria may influence the level at which SAMA will set the multiplication factor referred to in 7.14 (Alpha) above. Only those banks in full compliance with the qualitative criteria will be eligible for application of the minimum multiplication factor. The qualitative criteria include:
(1) The bank must conduct a regular program of backtesting, i.e. an ex-post comparison of the risk measures generated by the model against realized risk measures, as well as comparing hypothetical changes based on static positions with realized measures. “Risk measures” in this context, refers not only to Effective EPE, the risk measure used to derive regulatory capital, but also to the other risk measures used in the calculation of Effective EPE such as the exposure distribution at a series of future dates, the positive exposure distribution at a series of future dates, the market risk factors used to derive those exposures and the values of the constituent trades of a portfolio.
(2) The bank must carry out an initial validation and an on-going periodic review of its IMM model and the risk measures generated by it. The validation and review must be independent of the model developers.
(3) The board of directors and senior management should be actively involved in the risk control process and must regard credit and counterparty credit risk control as an essential aspect of the business to which significant resources need to be devoted. In this regard, the daily reports prepared by the independent risk control unit must be reviewed by a level of management with sufficient seniority and authority to enforce both reductions of positions taken by individual traders and reductions in the bank’s overall risk exposure.
(4) The bank’s internal risk measurement exposure model must be closely integrated into the day-to-day risk management process of the bank. Its output should accordingly be an integral part of the process of planning, monitoring and controlling the bank’s counterparty credit risk profile.
(5) The risk measurement system should be used in conjunction with internal trading and exposure limits. In this regard, exposure limits should be related to the bank’s risk measurement model in a manner that is consistent over time and that is well understood by traders, the credit function and senior management.
(6) Banks should have a routine in place for ensuring compliance with a documented set of internal policies, controls and procedures concerning the operation of the risk measurement system. The bank’s risk measurement system must be well documented, for example, through a risk management manual that describes the basic principles of the risk management system and that provides an explanation of the empirical techniques used to measure counterparty credit risk.
(7) An independent review of the risk measurement system should be carried out regularly in the bank’s own internal auditing process. This review should include both the activities of the business trading units and of the independent risk control unit. A review of the overall risk management process should take place at regular intervals (ideally no less than once a year) and should specifically address, at a minimum:
(a) The adequacy of the documentation of the risk management system and process;
(b) The organization of the risk control unit;
(c) The integration of counterparty credit risk measures into daily risk management;
(d) The approval process for counterparty credit risk models used in the calculation of counterparty credit risk used by front office and back office personnel;
(e) The validation of any significant change in the risk measurement process;
(f) The scope of counterparty credit risks captured by the risk measurement model;
(g) The integrity of the management information system;
(h) The accuracy and completeness of position data;
(i) The verification of the consistency, timeliness and reliability of data sources used to run internal models, including the independence of such data sources;
(j) The accuracy and appropriateness of volatility and correlation assumptions;
(k) The accuracy of valuation and risk transformation calculations; and
(l) The verification of the model’s accuracy as described below in 7.29 to 7.33.
(8) The on-going validation of counterparty credit risk models, including backtesting, must be reviewed periodically by a level of management with sufficient authority to decide the course of action that will be taken to address weaknesses in the models.
7.29. Banks must document the process for initial and on-going validation of their IMM model to a level of detail that would enable a third party to recreate the analysis. Banks must also document the calculation of the risk measures generated by the models to a level of detail that would allow a third party to recreate the risk measures. This documentation must set out the frequency with which backtesting analysis and any other on-going validation will be conducted, how the validation is conducted with respect to dataflows and portfolios and the analyses that are used.
7.30. Banks must define criteria with which to assess their EPE models and the models that input into the calculation of EPE and have a written policy in place that describes the process by which unacceptable performance will be determined and remedied.
7.31. Banks must define how representative counterparty portfolios are constructed for the purposes of validating an EPE model and its risk measures.
7.32. When validating EPE models and its risk measures that produce forecast distributions, validation must assess more than a single statistic of the model distribution.
7.33. As part of the initial and on-going validation of an IMM model and its risk measures, the following requirements must be met:
(1) A bank must carry out backtesting using historical data on movements in market risk factors prior to SAMA approval. Backtesting must consider a number of distinct prediction time horizons out to at least one year, over a range of various start (initialization) dates and covering a wide range of market conditions.
(2) Banks must backtest the performance of their EPE model and the model’s relevant risk measures as well as the market risk factor predictions that support EPE. For collateralized trades, the prediction time horizons considered must include those reflecting typical margin periods of risk applied in collateralized/margined trading, and must include long time horizons of at least 1 year.
(3) The pricing models used to calculate counterparty credit risk exposure for a given scenario of future shocks to market risk factors must be tested as part of the initial and on-going model validation process. These pricing models may be different from those used to calculate Market Risk over a short horizon. Pricing models for options must account for the nonlinearity of option value with respect to market risk factors.
(4) An EPE model must capture transaction specific information in order to aggregate exposures at the level of the netting set. Banks must verify that transactions are assigned to the appropriate netting set within the model.
(5) Static, historical backtesting on representative counterparty portfolios must be a part of the validation process. At regular intervals as directed by SAMA, a bank must conduct such backtesting on a number of representative counterparty portfolios. The representative portfolios must be chosen based on their sensitivity to the material risk factors and correlations to which the bank is exposed. In addition, IMM banks need to conduct backtesting that is designed to test the key assumptions of the EPE model and the relevant risk measures, e.g. the modelled relationship between tenors of the same risk factor, and the modelled relationships between risk factors.
(6) Significant differences between realized exposures and the forecast distribution could indicate a problem with the model or the underlying data that SAMA would require the bank to correct. Under such circumstances, SAMA may require additional capital to be held while the problem is being solved.
(7) The performance of EPE models and its risk measures must be subject to good backtesting practice. The backtesting program must be capable of identifying poor performance in an EPE model’s risk measures.
(8) Banks must validate their EPE models and all relevant risk measures out to time horizons commensurate with the maturity of trades for which exposure is calculated using an internal models method.
(9) The pricing models used to calculate counterparty exposure must be regularly tested against appropriate independent benchmarks as part of the on-going model validation process.
(10) The on-going validation of a bank’s EPE model and the relevant risk measures include an assessment of recent performance.
(11) The frequency with which the parameters of an EPE model are updated needs to be assessed as part of the validation process.
(12) Under the IMM, a measure that is more conservative than the metric used to calculate regulatory EAD for every counterparty, may be used in place of alpha times Effective EPE with the prior approval of SAMA. The degree of relative conservatism will be assessed upon initial SAMA approval and at the regular supervisory reviews of the EPE models. The bank must validate the conservatism regularly.
(13) The on-going assessment of model performance needs to cover all counterparties for which the models are used.
(14) The validation of IMM models must assess whether or not the bank level and netting set exposure calculations of EPE are appropriate.
Operational requirements for EPE models
7.34. In order to be eligible to adopt an internal model for estimating EPE arising from CCR for regulatory capital purposes, a bank must meet the following operational requirements. These include meeting the requirements related to the qualifying standards on CCR Management, a use test, stress testing, identification of wrong way risk, and internal controls.
Qualifying standards on CCR Management
7.35. The bank must satisfy SAMA that, in addition to meeting the operational requirements identified in 7.36 to 7.60 below, it adheres to sound practices for CCR management, including those specified in Counterparty credit risks section of the Credit Risk chapter of the Supervisory Review Process in the Basel Framework.
Use test
7.36. The distribution of exposures generated by the internal model used to calculate effective EPE must be closely integrated into the day-to-day CCR management process of the bank. For example, the bank could use the peak exposure from the distributions for counterparty credit limits or expected positive exposure for its internal allocation of capital. The internal model’s output must accordingly play an essential role in the credit approval, counterparty credit risk management, internal capital allocations, and corporate governance of banks that seek approval to apply such models for capital adequacy purposes. Models and estimates designed and implemented exclusively to qualify for the internal models method (IMM) are not acceptable.
7.37. A bank must have a credible track record in the use of internal models that generate a distribution of exposures to CCR. Thus, the bank must demonstrate that it has been using an internal model to calculate the distributions of exposures upon which the EPE calculation is based that meets broadly the minimum requirements for at least one year prior to SAMA approval.
7.38. Banks employing the internal models method must have an independent control unit that is responsible for the design and implementation of the bank’s CCR management system, including the initial and on-going validation of the internal model. This unit must control input data integrity and produce and analyze daily reports on the output of the bank’s risk measurement model, including an evaluation of the relationship between measures of CCR risk exposure and credit and trading limits. This unit must be independent from business credit and trading units; it must be adequately staffed; it must report directly to senior management of the bank. The work of this unit should be closely integrated into the day-to-day credit risk management process of the bank. Its output should accordingly be an integral part of the process of planning, monitoring and controlling the bank’s credit and overall risk profile.
7.39. Banks applying the internal models method must have a collateral management unit that is responsible for calculating and making margin calls, managing margin call disputes and reporting levels of independent amounts, initial margins and variation margins accurately on a daily basis. This unit must control the integrity of the data used to make margin calls, and ensure that it is consistent and reconciled regularly with all relevant sources of data within the bank. This unit must also track the extent of reuse of collateral (both cash and non-cash) and the rights that the bank gives away to its respective counterparties for the collateral that it posts. These internal reports must indicate the categories of collateral assets that are reused, and the terms of such reuse including instrument, credit quality and maturity. The unit must also track concentration to individual collateral asset classes accepted by the banks. Senior management must allocate sufficient resources to this unit for its systems to have an appropriate level of operational performance, as measured by the timeliness and accuracy of outgoing calls and response time to incoming calls. Senior management must ensure that this unit is adequately staffed to process calls and disputes in a timely manner even under severe market crisis, and to enable the bank to limit its number of large disputes caused by trade volumes.
7.40. The bank's collateral management unit must produce and maintain appropriate collateral management information that is reported on a regular basis to senior management. Such internal reporting should include information on the type of collateral (both cash and non-cash) received and posted, as well as the size, aging and cause for margin call disputes. This internal reporting should also reflect trends in these figures.
7.41. A bank employing the internal models method must ensure that its cash management policies account simultaneously for the liquidity risks of potential incoming margin calls in the context of exchanges of variation margin or other margin types, such as initial or independent margin, under adverse market shocks, potential incoming calls for the return of excess collateral posted by counterparties, and calls resulting from a potential downgrade of its own public rating. The bank must ensure that the nature and horizon of collateral reuse is consistent with its liquidity needs and does not jeopardize its ability to post or return collateral in a timely manner.
7.42. The internal model used to generate the distribution of exposures must be part of a counterparty risk management framework that includes the identification, measurement, management, approval and internal reporting of counterparty risk.27 This Framework must include the measurement of usage of credit lines (aggregating counterparty exposures with other credit exposures) and economic capital allocation. In addition to EPE (a measure of future exposure), a bank must measure and manage current exposures. Where appropriate, the bank must measure current exposure gross and net of collateral held. The use test is satisfied if a bank uses other counterparty risk measures, such as peak exposure or potential future exposure (PFE), based on the distribution of exposures generated by the same model to compute EPE.
7.43. A bank is not required to estimate or report EE daily, but to meet the use test it must have the systems capability to estimate EE daily, if necessary, unless it demonstrates to SAMA that its exposures to CCR warrant some less frequent calculation. It must choose a time profile of forecasting horizons that adequately reflects the time structure of future cash flows and maturity of the contracts. For example, a bank may compute EE on a daily basis for the first ten days, once a week out to one month, once a month out to eighteen months, once a quarter out to five years and beyond five years in a manner that is consistent with the materiality and composition of the exposure.
7.44. Exposure must be measured out to the life of all contracts in the netting set (not just to the one year horizon), monitored and controlled. The bank must have procedures in place to identify and control the risks for counterparties where exposure rises beyond the one-year horizon. Moreover, the forecasted increase in exposure must be an input into the bank’s internal economic capital model.
Stress testing
7.45. A bank must have in place sound stress testing processes for use in the assessment of capital adequacy. These stress measures must be compared against the measure of EPE and considered by the bank as part of its internal capital adequacy assessment process. Stress testing must also involve identifying possible events or future changes in economic conditions that could have unfavorable effects on a bank’s credit exposures and assessment of the bank’s ability to withstand such changes. Examples of scenarios that could be used are;
(i) economic or industry downturns,
(ii) market-place events, or
(iii) decreased liquidity conditions.
7.46. Banks must have a comprehensive stress testing program for counterparty credit risk. The stress testing program must include the following elements:
(1) Banks must ensure complete trade capture and exposure aggregation across all forms of counterparty credit risk (not just OTC derivatives) at the counterparty-specific level in a sufficient time frame to conduct regular stress testing.
(2) For all counterparties, banks should produce, at least monthly, exposure stress testing of principal market risk factors (e.g. interest rates, FX, equities, credit spreads, and commodity prices) in order to proactively identify, and when necessary, reduce outsized concentrations to specific directional sensitivities.
(3) Banks should apply multifactor stress testing scenarios and assess material non-directional risks (i.e. yield curve exposure, basis risks, etc.) at least quarterly. Multiple-factor stress tests should, at a minimum, aim to address scenarios in which a) severe economic or market events have occurred; b) broad market liquidity has decreased significantly; and c) the market impact of liquidating positions of a large financial intermediary. These stress tests may be part of bank-wide stress testing.
(4) Stressed market movements have an impact not only on counterparty exposures, but also on the credit quality of counterparties. At least quarterly, banks should conduct stress testing applying stressed conditions to the joint movement of exposures and counterparty creditworthiness.
(5) Exposure stress testing (including single factor, multifactor and material non-directional risks) and joint stressing of exposure and creditworthiness should be performed at the counterparty-specific, counterparty group (e.g. industry and region), and aggregate bank-wide CCR levels.
(6) Stress tests results should be integrated into regular reporting to senior management. The analysis should capture the largest counterparty-level impacts across the portfolio, material concentrations within segments of the portfolio (within the same industry or region), and relevant portfolio and counterparty specific trends.
(7) The severity of factor shocks should be consistent with the purpose of the stress test. When evaluating solvency under stress, factor shocks should be severe enough to capture historical extreme market environments and/or extreme but plausible stressed market conditions. The impact of such shocks on capital resources should be evaluated, as well as the impact on capital requirements and earnings. For the purpose of day-to-day portfolio monitoring, hedging, and management of concentrations, banks should also consider scenarios of lesser severity and higher probability.
(8) Banks should consider reverse stress tests to identify extreme, but plausible, scenarios that could result in significant adverse outcomes.
(9) Senior management must take a lead role in the integration of stress testing into the risk management framework and risk culture of the bank and ensure that the results are meaningful and proactively used to manage counterparty credit risk. At a minimum, the results of stress testing for significant exposures should be compared to guidelines that express the bank’s risk appetite and elevated for discussion and action when excessive or concentrated risks are present.
Wrong-way risk
7.47. Banks must identify exposures that give rise to a greater degree of general wrong-way risk. Stress testing and scenario analyses must be designed to identify risk factors that are positively correlated with counterparty credit worthiness. Such testing needs to address the possibility of severe shocks occurring when relationships between risk factors have changed. Banks should monitor general wrong way risk by product, by region, by industry, or by other categories that are germane to the business. Reports should be provided to senior management, the appropriate committee of the Board, or the delegated authority of the board on a regular basis that communicate wrong way risks and the steps that are being taken to manage that risk.
7.48. A bank is exposed to “specific wrong-way risk” if future exposure to a specific counterparty is highly correlated with the counterparty’s probability of default. For example, a company writing put options on its own stock creates wrong-way exposures for the buyer that is specific to the counterparty. A bank must have procedures in place to identify, monitor and control cases of specific wrong way risk, beginning at the inception of a trade and continuing through the life of the trade. To calculate the CCR capital requirement, the instruments for which there exists a legal connection between the counterparty and the underlying issuer, and for which specific wrong way risk has been identified, are not considered to be in the same netting set as other transactions with the counterparty. Furthermore, for single-name credit default swaps where there exists a legal connection between the counterparty and the underlying issuer, and where specific wrong way risk has been identified, EAD in respect of such swap counterparty exposure equals the full expected loss in the remaining fair value of the underlying instruments assuming the underlying issuer is in liquidation. The use of the full expected loss in remaining fair value of the underlying instrument allows the bank to recognize, in respect of such swap, the market value that has been lost already and any expected recoveries. Accordingly LGD for advanced or foundation IRB banks must be set to 100% for such swap transactions.28 For banks using the Standardized Approach, the risk weight to use is that of an unsecured transaction. For equity derivatives, bond options, securities financing transactions etc. referencing a single company where there exists a legal connection between the counterparty and the underlying company, and where specific wrong way risk has been identified, EAD equals the value of the transaction under the assumption of a jump-to-default of the underlying security. Inasmuch this makes re-use of possibly existing (market risk) calculations (for incremental risk charge) that already contain an LGD assumption, the LGD must be set to 100%.
Integrity of modelling process
7.49. Other operational requirements focus on the internal controls needed to ensure the integrity of model inputs; specifically, the requirements address the transaction data, historical market data, frequency of calculation, and valuation models used in measuring EPE.
7.50. The internal model must reflect transaction terms and specifications in a timely, complete, and conservative fashion. Such terms include, but are not limited to, contract notional amounts, maturity, reference assets, collateral thresholds, margining arrangements, netting arrangements, etc. The terms and specifications must reside in a secure database that is subject to formal and periodic audit. The process for recognizing netting arrangements must require signoff by legal staff to verify the legal enforceability of netting and be input into the database by an independent unit. The transmission of transaction terms and specifications data to the internal model must also be subject to internal audit and formal reconciliation processes must be in place between the internal model and source data systems to verify on an ongoing basis that transaction terms and specifications are being reflected in EPE correctly or at least conservatively.
7.51. When the Effective EPE model is calibrated using historic market data, the bank must employ current market data to compute current exposures and at least three years of historical data must be used to estimate parameters of the model. Alternatively, market implied data may be used to estimate parameters of the model. In all cases, the data must be updated quarterly or more frequently if market conditions warrant. To calculate the Effective EPE using a stress calibration, the bank must also calibrate Effective EPE using three years of data that include a period of stress to the credit default spreads of a bank’s counterparties or calibrate Effective EPE using market implied data from a suitable period of stress. The following process will be used to assess the adequacy of the stress calibration:
(1) The bank must demonstrate, at least quarterly, that the stress period coincides with a period of increased credit default swaps (CDS)or other credit spreads - such as loan or corporate bond spreads - for a representative selection of the bank’s counterparties with traded credit spreads. In situations where the bank does not have adequate credit spread data for a counterparty, the bank should map each counterparty to specific credit spread data based on region, internal rating and business types.
(2) The exposure model for all counterparties must use data, either historic or implied, that include the data from the stressed credit period, and must use such data in a manner consistent with the method used for the calibration of the Effective EPE model to current data.
(3) To evaluate the effectiveness of its stress calibration for Effective EPE, the bank must create several benchmark portfolios that are vulnerable to the same main risk factors to which the bank is exposed. The exposure to these benchmark portfolios shall be calculated using:
(a) current positions at current market prices, stressed volatilities, stressed correlations and other relevant stressed exposure model inputs from the 3-year stress period and
(b) current positions at end of stress period market prices, stressed volatilities, stressed correlations and other relevant stressed exposure model inputs from the 3-year stress period. SAMA may adjust the stress calibration if the exposures of these benchmark portfolios deviate substantially.
7.52. For a bank to recognize in its EAD calculations for OTC derivatives the effect of collateral other than cash of the same currency as the exposure itself, if it is not able to model collateral jointly with the exposure then it must use the standard supervisory haircuts of the comprehensive approach.
7.53. If the internal model includes the effect of collateral on changes in the market value of the netting set, the bank must model collateral other than cash of the same currency as the exposure itself jointly with the exposure in its EAD calculations for securities-financing transactions.
7.54. The EPE model (and modifications made to it) must be subject to an internal model validation process. The process must be clearly articulated in banks’ policies and procedures. The validation process must specify the kind of testing needed to ensure model integrity and identify conditions under which assumptions are violated and may result in an understatement of EPE. The validation process must include a review of the comprehensiveness of the EPE model, for example such as whether the EPE model covers all products that have a material contribution to counterparty risk exposures.
7.55. The use of an internal model to estimate EPE, and hence the exposure amount or EAD, of positions subject to a CCR capital requirement will be conditional upon the explicit approval of SAMA. SAMA and relevant supervisory authorities of banks that carry out material trading activities in multiple jurisdictions will work co-operatively to ensure an efficient approval process.
7.56. SAMA will require that banks seeking to make use of internal models to estimate EPE meet the requirements regarding, for example, the integrity of the risk management system, the skills of staff that will rely on such measures in operational areas and in control functions, the accuracy of models, and the rigour of internal controls over relevant internal processes. As an example, banks seeking to make use of an internal model to estimate EPE must demonstrate that they meet the general criteria for banks seeking to make use of internal models to assess market risk exposures, but in the context of assessing counterparty credit risk.29
7.57. The supervisory review process (SRP) standard of this framework provides general background and specific guidance to cover counterparty credit risks that may not be fully covered by the Pillar 1 process.
7.58. No particular form of model is required to qualify to make use of an internal model. Although this text describes an internal model as a simulation model, other forms of models, including analytic models, are acceptable subject to SAMA approval and review. Banks that seek recognition for the use of an internal model that is not based on simulations must demonstrate to SAMA that the model meets all operational requirements.
7.59. For a bank that qualifies to net transactions,
(1) The bank must have internal procedures to verify that, prior to including a transaction in a netting set,
(2) The transaction is covered by a legally enforceable netting contract that meets the applicable requirements of the standardized approach to counterparty credit risk (in Chapter 6 of this framework), chapter 9 of the Minimum Capital Requirements for Credit Risk, or the Cross Product Netting Rules set forth 7.61 to 7.71 below in this framework.
7.60. For a bank that makes use of collateral to mitigate its CCR, the bank must have internal procedures to verify that, prior to recognizing the effect of collateral in its calculations, the collateral meets the appropriate legal certainty standards as set out in chapter 9 of the Minimum Capital Requirements for Credit Risk.
Cross-product netting rules
7.61. The Cross-Product Netting Rules apply specifically to netting across SFTs, or to netting across both SFTs and OTC derivatives, for purposes of regulatory capital computation under IMM.
7.62. Banks that receive approval to estimate their exposures to CCR using the internal models method may include within a netting set SFTs, or both SFTs and OTC derivatives subject to a legally valid form of bilateral netting that satisfies the following legal and operational criteria for a Cross-Product Netting Arrangement (as defined below). The bank must also have satisfied any prior approval or other procedural requirements that SAMA determines to implement for purposes of recognizing a Cross-Product Netting Arrangement.
Legal Criteria
7.63. The bank has executed a written, bilateral netting agreement with the counterparty that creates a single legal obligation, covering all included bilateral master agreements and transactions (“Cross-Product Netting Arrangement”), such that the bank would have either a claim to receive or obligation to pay only the net sum of the positive and negative
(i) close-out values of any included individual master agreements and
(ii) mark-to-market values of any included individual transactions (the “Cross-Product Net Amount”), in the event a counterparty fails to perform due to any of the following: default, bankruptcy, liquidation or similar circumstances.
7.64. The bank has written and reasoned legal opinions that conclude with a high degree of certainty that, in the event of a legal challenge, relevant courts or administrative authorities would find the bank’s exposure under the Cross Product Netting Arrangement to be the Cross-Product Net Amount under the laws of all relevant jurisdictions. In reaching this conclusion, legal opinions must address the validity and enforceability of the entire Cross-Product Netting Arrangement under its terms and the impact of the Cross-Product Netting Arrangement on the material provisions of any included bilateral master agreement.
(1) The laws of “all relevant jurisdictions” are: (i) the law of the jurisdiction in which the counterparty is chartered and, if the foreign branch of a counterparty is involved, then also under the law of the jurisdiction in which the branch is located, (ii) the law that governs the individual transactions, and (iii) the law that governs any contract or agreement necessary to effect the netting.
(2) A legal opinion must be generally recognized as such by the legal community in the bank’s home country or a memorandum of law that addresses all relevant issues in a reasoned manner.
7.65. The bank has internal procedures to verify that, prior to including a transaction in a netting set, the transaction is covered by legal opinions that meet the above criteria.
7.66. The bank undertakes to update legal opinions as necessary to ensure continuing enforceability of the Cross-Product Netting Arrangement in light of possible changes in relevant law.
7.67. The Cross-Product Netting Arrangement does not include a walkaway clause. A walkaway clause is a provision which permits a non-defaulting counterparty to make only limited payments, or no payment at all, to the estate of the defaulter, even if the defaulter is a net creditor.
7.68. Each included bilateral master agreement and transaction included in the Cross Product Netting Arrangement satisfies applicable legal requirements for recognition of credit risk mitigation techniques in credit risk mitigation techniques in chapter 9 of the Minimum Capital Requirements for Credit Risk.
7.69. The bank maintains all required documentation in its files.
Operational Criteria
7.70. SAMA is satisfied that the effects of a Cross-Product Netting Arrangement are factored into the bank’s measurement of a counterparty’s aggregate credit risk exposure and that the bank manages its counterparty credit risk on such basis.
7.71. Credit risk to each counterparty is aggregated to arrive at a single legal exposure across products covered by the Cross-Product Netting Arrangement. This aggregation must be factored into credit limit and economic capital processes.
27 This section draws heavily on the Counterparty Risk Management Policy Group's paper, Improving Counterparty Risk Management Practices (June 1999).
28 Note that the recoveries may also be possible on the underlying instrument beneath such swap. The capital requirements for such underlying exposure are to be calculated without reduction for the swap which introduces wrong way risk. Generally this means that such underlying exposure will receive the risk weight and capital treatment associated with an unsecured transaction (i.e. assuming such underlying exposure is an unsecured credit exposure).
29 See Chapter 10.1 to Chapter 10.4 of the Minimum Capital Requirements for Market Risk.

