Annexes
Annex A. Glossary
The following list contains a definition of the main terms used in this document.
Glossary Term Description Application A software program hosted by an information system.
Source: NISTIR 7298 3Glossary of Key Information Security Terms
Asset The data, personnel, devices, systems, and facilities that enable the organization to achieve business purposes.
Source: NISTIR 7298 3Glossary of Key Information Security Terms
Attacker Refer to "Threat actor". (Threat actor) Capability Resources and skills of a threat actor. Cyber risk The risk to organizational operations (including mission, functions, image, reputation), organizational assets, individuals, other organizations, and the nation due to the potential for unauthorized access, use, disclosure, disruption, modification, or destruction of information and/or information systems.
Source: NISTIR 7298 3Glossary of Key information Security Terms
Cybersecurity Cybersecurity is defined as the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance, and technologies that can be used to protect the Member Organization's information assets against internal and external threats. Cyber threat intelligence (CTI) Threat information that has been aggregated, transformed, analyzed, interpreted, or enriched to provide the necessary context for decision-making processes.
Source: NISTIR 7298 3Glossary of Key Information Security Terms
(Cybersecurity) Incident An occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.
Source: NISTIR 7298 3Glossary of Key Information Security Terms
indicator of Compromise (loC) Indicators of compromise serve as forensic evidence of potential intrusions on a host system or network. (Threat actor) Intent
The desire of a threat actor to target a particular entity. Threat actors are usually rational actors operating with a clear purpose (e.g. espionage, data theft/exfiltration, extortion, destruction, disruption, supply chain compromise). Kill Chain Adopted from the military, the kill chain was developer by Lockheed Martin to identify and taxonomize the various phases of a cyber attack (Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, Actions upon Objectives). Malware
Hardware, firmware, or software that is intentionally included or inserted in a system for a harmful purpose.
Source: NISTIR 7298 3Glossary of Key information Security Terms
MITRE ATT&CK An open source framework developed by MITRE taxonomizing tactics, techniques, and procedures used by threat actors when conducting cyber attacks. Member Organization Any regulated entity supervised and regulated by SAMA. Modus Operandi A method of procedure, especially referred to a distinct pattern or method of operation that indicates or suggests the work of a single criminal in more than one crime. Motivation The type of benefit or harm a threat actor ultimately wants to achieve with its actions. Network Information system(s) implemented with a collection of interconnected components. Such components may include routers, hubs, cabling, telecommunications controllers, key distribution centers, and technical control devices.
Source: NISTIR 7298 3Glossary of Key Information Security Terms
Open Source Intelligence (OSINT) Relevant information derived from the systematic collection, processing, and analysis of publicly available information in response to known or anticipated intelligence requirements. Organization Company, entity, or group of people that works together for a particular purpose. (Threat actor) Origin Country from which the threat actor launches its attacks. The origin of a threat actor cannot always be determined with sufficient precision because they tend to cover their tracks. Procedure Procedures are the specific implementation the threat actor uses for techniques.
Source: MITRE ATT&CK
Process A set of interrelated or interacting activities which transforms inputs into outputs. Ransomware A form of malware designed to deny access to a computer system or data until ransom is paid. A user of a system infected with ransomware is usually confronted with an extortion message (in many cases a windows popup) asking the victim to pay a ransom fee to the threat actor (usually in cryptocurrency) in order to regain access to their system and data. Red team (exercise) An exercise, reflecting real-world conditions, that is conducted as a simulated adversarial attempt to compromise organizational missions and/or business processes to provide a comprehensive assessment of the security capability of the information system and organization.
Source: NIST SP 1800 21B Glossary of Key Information Security Terms
(Threat actor) Resources Resources measure the scope, intensity, sustainability, and diversity of the total set of actions that a threat actor can take. Sector One of the areas in which the economic activity of a country is divided. Service A capability or function provided by an entity.
Source: NISTIR 7298 3Glossary of Key Information Security Terms
(Threat actor) Skill The extent to which a threat actor is able to leverage technical means (e.g. create custom malware) and operates with awareness, intelligence, learning potential, problem solving, decision-making coherence, and operational experience. Stakeholder One who is involved in or affected by a course of action. Strategic threat intelligence The level of threat intelligence focused on objectives, motivations and intents of cyber threat actors. It aims at examining attributions to cyber threat actors, investigating real motivations and links between cyber events, and understanding complex systems dynamics and trends. Geopolitical, sectorial and context analysis is a fundamental tool. Tactic The threat actor's tactical goal: the reason for performing an action.
Source: MITRE ATT&CK
(Threat actor) Target The choices that actors make in terms of the target(s) of their attacks. A threat actor selects a target based on location, sector, and the types of information processed and attack surface available. The geopolitical landscape plays a key role in the targeting pattern of nation state actors. Taxonomy A classification of interrelated elements. Technique Techniques represent "how" a threat actor achieves a tactical goal by performing an action.
Source: MITRE ATT&CK
(Cyber security) Threat Any circumstance or event with the potential to adversely impact organizational operations, organizational assets, individuals, other organizations, or the nation through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service.
Source: NISTIR 7298 3Glossary of Key Information Security Terms
Threat actor Individuals, groups, organizations, or states that seek to exploit the organization's dependence on cyber resources (i.e., information in electronic form, information and communications technologies, and the communications and information-handling capabilities provided by those technologies)" (NIST 2012) or, more in general, "An individual or a group posing a threat" (NIST 2016). Threat landscape A collection of threats in a particular domain or context, with information on identified vulnerable assets, threats, risks, threat actors and observed trends.
Source: ENISA
Threat intelligence requirement Threat intelligence requirements guide the intelligence production effort efficiently and establish what intelligence should be produced to meet the security objectives of an Organization. (Threat actor) Type Grouping of threat actors who share similar characteristics, such as similar intents and motivations, and operate in similar ways. Unified Kill Chain An evolution of the kill chain framework detailing the phases of an attack. (Attack) Vector General approach for achieving an impact, taking advantage of the exposure of a type of, or a region in, an attack surface. Annex B. Areas of Analysis
Member Organizations should develop threat intelligence requirements based on different areas of analysis which are relevant to their business priorities. These areas of analysis may vary depending on Member Organizations including but not limited to:
Geopolitics: this includes requirements to identify geopolitical events that might determine a cybersecurity attack within the scope of analysis, such as large global campaigns carried out by threat actors, significant past relevant cybersecurity incidents, etc.
Threat actor: this includes requirements to identify the main threat actors on which the organization should be particularly focused on.
Threat vectors: this includes requirements to identify relevant attack techniques (e.g. initial access vectors, etc.).
Technology: this includes requirements to evaluate possible attacks against technologies that the organisation rely upon.
Industry: this includes requirements to identify possible attacks against industries relevant to the organization (e.g. third parties in the supply chain or national critical infrastructure).
Annex C. Types of Sources
The following tables contain examples of internal and external sources.
Sources Type of sources Public sector Threat intelligence provided by SAMA and the National Cybersecurity Authority (NCA) National civil or government bodies (e.g. law enforcement) Reports or information from other sectorial or national authorities (e.g. CMA, FS-ISAC, Saudi CERT) Public frameworks (e g. ENISA, EUROPOL, MITRE) External sources Private sector Threat intelligence from specialized suppliers and platforms available upon subscription or contract Publicly available threat intelligence reports, news, briefs and analyses Academic sector Whitepapers Academic publications and conferences Academic journals Table 1. External sources
Sources Type of sources Internal
sources- Application and infrastructure logs
Intrusion Detection System (IDS)
Intrusion Prevention System (IPS)
Cyber security defence systems
Table 2 Internal sources
Annex D. Types of Intelligence
Currently, there is a wide range of different kinds of intelligence that could be used to obtain a holistic understanding of the threats that an organization faces.
These types of intelligence include:
OSINT: open source intelligence obtained from publicly available sources (e.g. Threat report, blog, etc.)
TECHINT: technical intelligence derived from signals generated routinely by hardware devices or software applications connected to an organization's network (e.g. loCs, malware analysis, code reports, etc.)
SOCMINT: social media intelligence, a process of identifying, gathering, validating, and analyzing data from social media sites and accounts (e.g. Blogs, microblogs, social networks, etc.)
HUMINT: human intelligence derived overtly or covertly from human sources based on a relationship between an intelligence analyst and the analyst's handler (e.g. active monitoring on forums)
Deep and Dark Web Intelligence: intelligence gathered on the deep and dark web (e.g. marketplaces, forums, etc.)
Annex E. Threat Intelligence Delivery Methods
Member Organizations should establish the delivery mechanism of the threat intelligence produced which includes, but is not limited to:
Cyber threat bulletins including cyber threat information that may be useful for the organizations
Simple alerts sent out by phone, text, or email
Detailed reports enriched with analysis, tables, numbers, graphics, and multimedia
Machine-readable data feeds based on a proprietary or open standard structured threat intelligence notation, for Security Information and Event Management (SIEM), anti-virus software, firewalls, intrusion prevention systems (IPS), intrusion detection systems (IDS) and forensic tools
Custom-designed output for in house systems
Application Programming Interfaces (APIs) enabling direct system connection for the purposes of intelligence query or retrieval
Secure online portals providing on-demand access to an up-to-date threat intelligence database and range of analytical functions that could be as basic as from simple queries to more complex data mining
Annex F. Intelligence Standard Operating Procedures
Below are listed some examples of how SOPs should help users when performing specific kind of threat intelligence.
When performing deep and dark web intelligence, the step-by-step instructions should help users in identifying all the elements needed to properly conduct it, including but not limited to:
Using a controlled isolated and untraceable environment such as a Virtual Machine (VM)
Update and collect a list of deep web and dark web forums and marketplaces
Create various avatars for access
Similarly, when performing Social Media Intelligence (SOCMINT), the step-by-step instructions should help in identifying all the elements needed to properly conduct it, for example:
Providing users with a list of different types of sources and continuously updating this list (e.g. Blogs, microblogs, social networks, images, video, and discussion forums)
Conduct training on Social network and online video hosting and sharing platform (e.g. Twitter, Facebook, YouTube etc.)
Using social media tools when possible (commercial and open-source)
In the same way, when performing human intelligence (HUMINT), the step-by-step instructions should help users in identifying all the elements needed to properly conduct it, including but not limited to:
Conduct ethics training for analysts performing active engagements online
Implement SOPs related to forum and marketplace accesses
Build an avatar for each access to avoid traceback
Understanding the difference between active and passive monitoring
Annex G. Analytical Approach
Member Organizations should adopt an analytical approach so the intelligence produced meets the intelligence requirements.
Based on what is most suitable for the Member Organizations, the analytical approach could be:
Hypothesis-driven: this approach includes the definition of a hypothesis and its evaluation by analyzing available information
Analyst-driven: this approach is based on the analyst's critical and analytical thinking
Contrarian: this approach aims at challenging the main conclusions or points made by the source to put forward a counter-argumentative approach
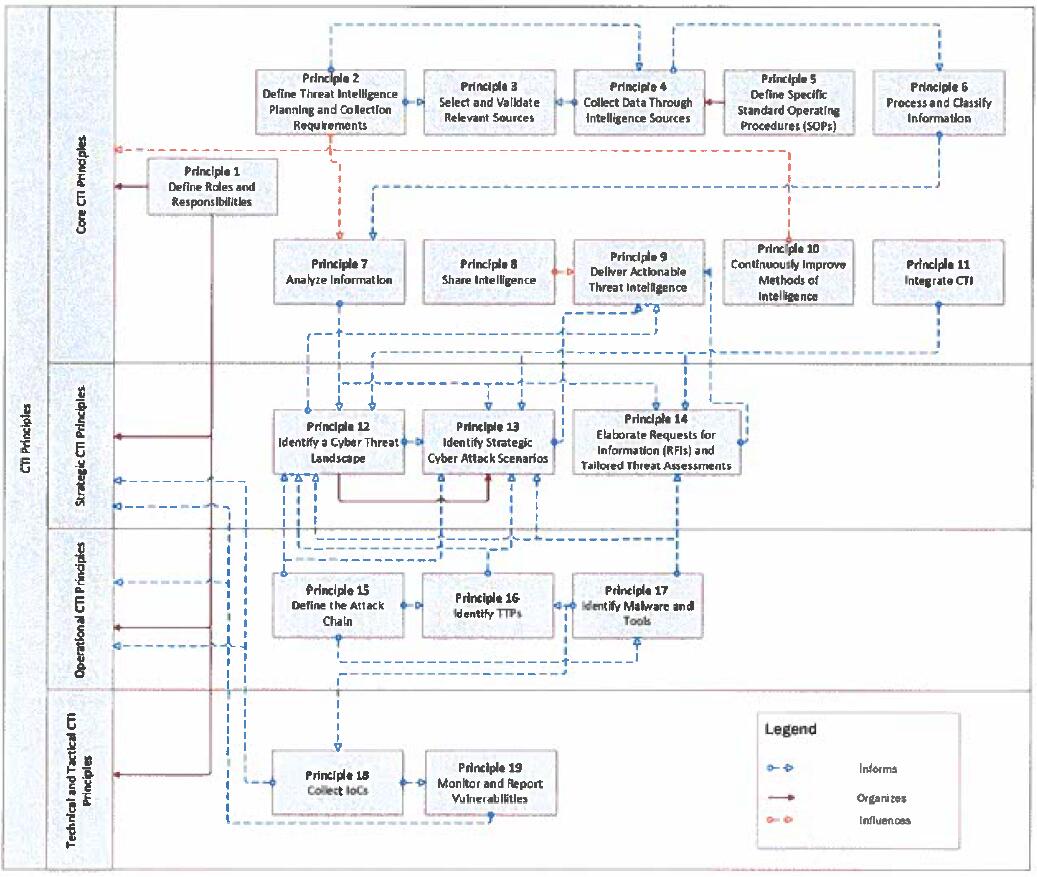
Annex H. CTI Principles High Level Graph
Below is represented a high-level graph of the CTI principles. The graph is aimed at representing the high-level structure of the document.
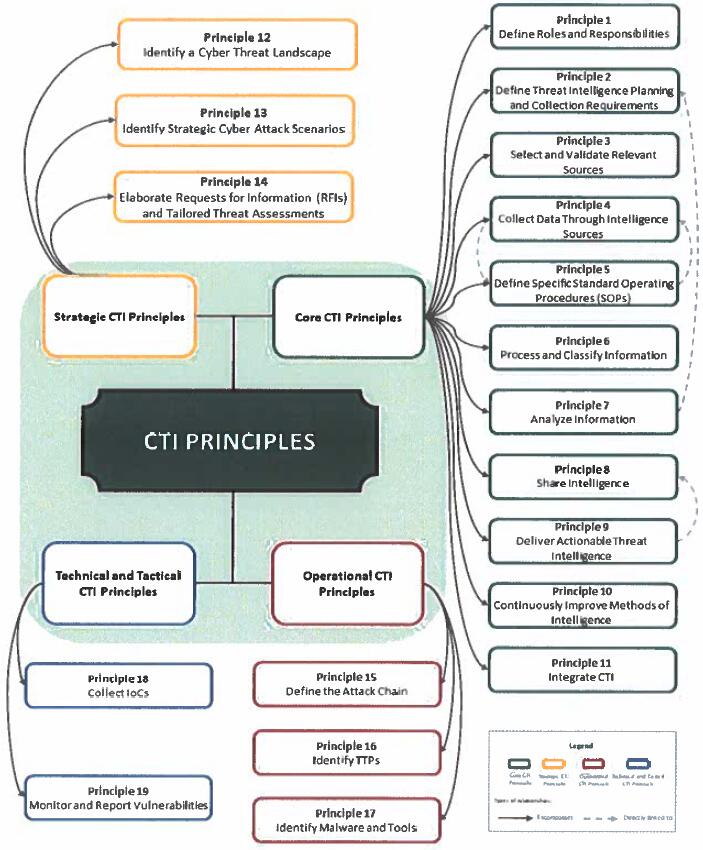
Annex J. CTI Principles Mind Map
Below is represented a mind map of the structure of the CTI principles. The graph is aimed to clearly represent the different domains of the document and how the principles are related to each other.