Cyber Threat Intelligence Principles
The Cyber Threat Intelligence (CTI) Principles describes best practices focused on producing, processing, and disseminating threat intelligence to enhance the identification and mitigation of cyber threats relevant to the financial sector in the KSA through actionable threat intelligence.
The structure of the document has been developed based on different types of CTI. The principles contained in each section (Core, strategic, Operational, and Technical and Tactical) have different purposes aiming at a holistic practice of CTI. In particular:
Core CTI Principles are a prerequisite to the practice of CTI and inform the other types of CTI. They include the activities needed to be performed for the planning, production, and dissemination of CTI.
Strategic CTI Principles involve a specialized CTI practice which include the activities needed to be performed for the identification of the objective, motivations, and intent of threat actors.
Operational CTI Principles involve a specialized CTI practice which include the activities needed to be performed for the identification of the modus operandi, behavior, and techniques used by threat actors.
Technical & Tactical CTI Principles involve a specialized CTI practice which include the activities needed to be performed for the identification of technical components and indicators of cyber attacks.
All principles should be applied by Member Organizations. The adoption of a phased approach for the complete implementation of the principles is at the discretion of the Member Organizations. The principles contained in this document apply also to the Member Organizations who outsource their CTI capability.
This document is organized in four domains including Core CTI, Strategic CTI, Operational CTI, and Technical and Tactical CTI as detailed in the graph below:
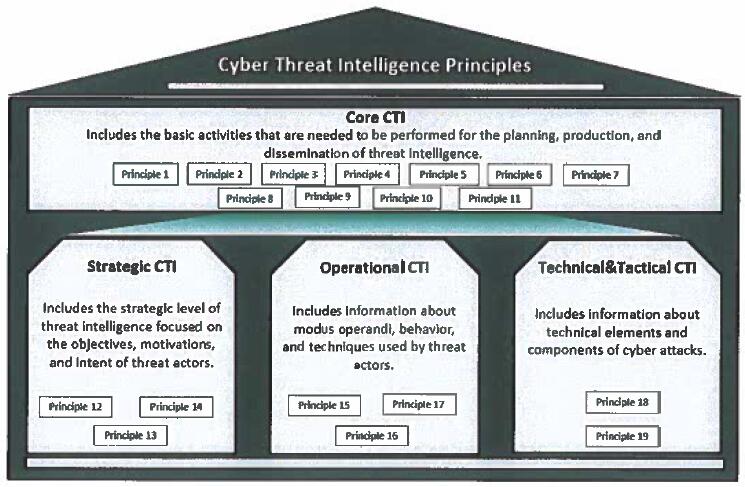
Figure 1. CTI Principles
Domain 1: Core Cyber Threat Intelligence Principles
Core Cyber Threat Intelligence Principles establish a baseline for the planning, collection, processing, analysis, and dissemination of threat intelligence based around the intelligence lifecycle framework.
The Core Threat Intelligence Principles section is based on the main phases of the intelligence lifecycle, including the dissemination of threat intelligence and continuously improving the CTI capability and performance of Member Organizations.
The intelligence lifecycle allows security teams to analyze and understand the information, prevent, and defend their networks from cyber attacks. It is the process by which raw data and information is identified, collected, and analyzed. Subsequently, raw data and information is transformed into intelligence to be used and actioned by Member Organizations. The intelligence lifecycle is fully represented by the following Core Principles.
Principle 1: Define Roles and Responsibilities
Member Organizations should define roles and responsibilities within the organization to produce threat intelligence with the expectation of creating their own CTI capability. This should include a dedicated team in charge of the production and dissemination of threat intelligence. In addition, the cyber threat intelligence team should be supported by skilled resources with purpose-specific advanced tools and a defined budget. Member Organizations should define communication channels inside the organization between the cyber threat intelligence team and other teams, including with stakeholders (e.g. Cyber security teams, business leaders, risk team, etc.) and with external organizations.
Principle 2: Define Threat Intelligence Planning and Collection Requirements
Member Organizations should develop a set of threat intelligence requirements to guide their intelligence production efforts efficiently and to establish what intelligence should be produced to meet their security and business objectives. To define such requirements, Member Organizations should define the scope of the analysis (e.g. organizational, sectorial, national, etc.) and consider different areas of analysis relevant to their business priorities (e.g. technology, threat actors, etc.). In addition, Member Organizations should ensure periodical review of the defined requirements. Further explanation of the areas of analysis is provided in "Annex B. Areas of Analysis“.
Principle 3: Select and Validate Relevant Sources
Member Organizations should select sources in line with the defined threat intelligence requirements. Moreover, Member Organizations should define what type of sources to use, understand which sources are likely to produce the desired information, and consider a wide range of different sources to enable them to build a holistic understanding of threats relevant to the financial sector. Additionally, Member Organizations should assess the reliability and reputation of every source considering specific parameters. These parameters include the quality and accuracy of information, timeliness in relation to reporting, technical information included, comprehensiveness of threat feed, and type of information aligned with the defined threat intelligence requirements.
Member Organizations should select sources that provide information that is relevant to their business and in line with the threat Intelligence requirements defined. These sources can be external or internal to the organization. Examples of internal and external sources are provided In "Annex C. Types of Sources”.
Principle 4: Collect Data Through Intelligence Sources
Member Organizations should collect data via various intelligence sources (e.g. OSINT, TECHINT, SOCMINT, HUMINT and deep web and dark web intelligence). Gathering information from a diverse range of sources will produce holistic assessments of threats faced by the organization. Examples of types of Intelligence are provided in "Annex D. Types of Intelligence". Specific Standard Operating Procedures (SOPs) to conduct intelligence should be followed as specified in "Annex F. Intelligence Standard Operating Procedures".
Principle 5: Define Specific Standard Operating Procedures (SOPs)
Member Organizations should define specific standard operating procedures (SOPs) when conducting specific types of intelligence as detailed in "Principle 4: Collect Data Through Intelligence Sources". Member Organizations should establish a set of instructions for individuals within the organizations to perform CTI to ensure functional procedures, while simultaneously reducing miscommunication and ambiguity. The SOPs should be detail-oriented and provide step-by-step instructions as to how analysts within Member Organizations must go about completing tasks and processes related to CTI. Examples of SOPs are provided in "Annex F. Intelligence Standard Operating Procedures".
Principle 6: Process and Classify Information
Member Organizations should process and classify collected intelligence - either manually, automatically, or a combination of the two - from the selected sources and store it securely. Furthermore, Member Organizations should refer to the "SAMA Cybersecurity Communication Protocols" when employing the Traffic Light Protocol (TLP) classification scheme for the collection and processing of information.
Principle 7: Analyze Information
Member Organizations should apply a variety of quantitative and qualitative analytical techniques to analyze the importance and implications of the processed information, and, in turn, produce actionable intelligence. Moreover, Member Organizations will combine and analyze various pieces of information, collected from diverse sources, to identify patterns, trends, and new developments relevant to the Member Organization.
Member Organizations should adopt adequate analytical approaches (e.g. Hypothesis-driven, Analyst-driven, and/or Contrarian) to be sure that the intelligence produced meets the intelligence requirements as defined in "Principle 2: Define Threat Intelligence Requirements". Examples of different types of analytical approaches are provided in "Annex G. Analytical Approach".
Principle 8: Share Intelligence
Member Organizations should establish specific sharing standards for the dissemination of threat intelligence. Examples of delivery methods for threat intelligence are provided in "Annex E,-Threat intelligence Delivery Methods".
Member Organizations should establish a consistent and precise language practice throughout the organization to ensure wide applicability of threat intelligence. To clearly communicate threat intelligence, the Member Organizations should rely for example on a writing guide (e.g. the Economist style Guide). They should also use a scale of 'estimative probability' system while engaging in analysis as defined in "SAMA's Threat Advisory Template".
Member Organizations should disseminate threat intelligence in an effective, timely, and accurate manner. It should be presented in a clear, concise, and coherent way when shared with the relevant internal stakeholders. When sharing intelligence with SAMA, Member Organizations should define procedures that help control the publication and distribution of threat information.
All the information produced by the Member Organizations should be classified in accordance with the Traffic Light Protocol (TLP) classification scheme as per the "SAMA Cybersecurity Communication Protocols".
Principle 9: Deliver Actionable Threat Intelligence
Member Organizations should implement relevant decisions and actions based on the intelligence produced to help build the resilience of the financial sector in the KSA. Member Organizations should take into consideration what actions are necessary, who is going to take these actions, and the response timeframe for anticipating or responding to an attack. Based on threat Intelligence produced, Member Organizations should take relevant mitigation actions or measures to improve defense infrastructure and resilience based on their knowledge of relevant threats (e.g. knowing techniques adopted by threat actors on a network could help Member Organizations to prioritize mitigation controls).
The Member Organization's threat intelligence team should share relevant intelligence with other relevant departments such as the Security Operations Center (SOC), IT, etc. sharing of such information should be done as per "Principle 8: Share Intelligence". These departments should also share information deemed relevant to the CTI capability as to feed and complement threat intelligence assessments.
Principle 10: Continuously Improve Methods of Intelligence
Member Organizations should continuously maintain, update, and improve the production, processing, analysis, and dissemination of threat intelligence with the aim of continuously increasing the maturity of the financial sector in the KSA. Additionally, Member Organizations should also regularly update existing threat intelligence requirements based on feedback from internal and external stakeholders, threat intelligence users, changes in the industry, and evolutions within the global threat landscape.
Member Organizations should perform periodic analysis of the threat information collected and verify its relevance (e.g. in terms of motivation, target, modus operandi, capability, etc.) according to assets and data processed by them. Member Organizations should also consider the services of a dedicated threat intelligence provider, who can offer relevant insights to complement the organization's existing understanding of threats.
Member Organizations should consider using Key Performance Indicators (KPIs), Key Risk Indicators (KRIs), and Objectives and Key Results (OKRs) to quantify progress and update intelligence practices and protocols as aligned to their internal procedures.
Principle 11: Integrate CTI
Member Organizations should consider integrating CTI in situational awareness and red teaming assessments in line with the "SAMA FEER Framework".
The Integration within situational awareness activities will help to build strategic understanding of cyber incidents, for example, identifying threat actors, trends in their activities, and objectives. Additionally, it will offer tactical understanding of events or situations in cyberspace and will facilitate effective and efficient decision-making in times of crisis.
Member Organizations should also take into consideration that the integration of CTI in red team assessments activities will help to get a better understanding of how cyber attackers gain access to networks and sensitive data. This can help to validate the organisation's security posture and help contextualise business process improvements by delivering more intelligence on cyber risks, their potential impact, and remediation options.
Domain 2: Strategic Cyber Threat Intelligence
Considering the changing nature of the threat landscape, Strategic CTI allows to continuously monitor the cyber ecosystem and to prevent threats.
Strategic CTI specifically helps at identifying and understanding the threats to the financial sector. It provides the level of threat intelligence focused on objectives, motivations, and intent of cyber threat actors, strategic CTI aims at examining attribution, investigating real motivations and links between cyber events, and understanding the financial sector's ecosystem.
The threat landscape includes information on the threat actors that are most relevant to the Member Organizations, their main characteristics, and the main cyber trends within the financial sector worldwide.
This information is addressed to relevant executive management (e.g. chief Information Security officer) who will relay the information to other relevant parties (e.g. IT management, business leaders, etc.). Strategic CTI aids in the organization's understanding of current cyber threats, unknown future threats, threat actors, and attribution of attacks. Such understanding is key to having a pro-active approach to cybersecurity in order to build the resilience of the financial sector in the KSA.
Principle 12: Identify a Cyber Threat Landscape
Member Organizations should identify the cyber threat landscape relevant to their organization and operations, with information on identified vulnerable assets, threats, risks, threat actors, and observed trends. This includes identifying events that can influence the financial sector's threat landscape.
Moreover, Member Organizations should identify the threat actors that may intend to target them, and their main characteristics including their origin, intent, motivation, and capabilities. After identifying their threat landscape, Member Organizations should perform an assessment of the identified threats to prioritize which are the most relevant. Additionally, Member Organizations should also identify the main cyber trends that are likely to influence the future evolutions of the cyber threat landscape.
Principle 13: Identify Strategic Cyber Attack Scenarios
Member Organizations should identify the strategic cyber attack scenarios that provide a realistic representation of likely cyber attacks against them. These scenarios should involve one or more threat actors, address one or more targets, and the potential impacts of the scenarios.
To elaborate strategic cyber attack scenarios, Member Organizations should identify similarities of features of threat actors or campaigns within the threat landscape outlined as per "Principle 12: Identify a Cyber Threat Landscape" (e.g. similar technique, similar attack type, etc.). In addition, Member Organizations should perform an assessment on the identified scenarios to prioritize the most likely and impactful scenarios and should take relevant corrective actions based on the threats and scenarios identified. The periodicity of the assessment of the identified scenarios should be defined by Member Organizations based on their own internal processes.
Principle 14: Elaborate Requests for Information (RFIs) and Tailored Threat Assessments
Member Organizations should be able to provide, upon request, detailed information (e.g. cyber threats, trends, events, and malware or tools) related to possible cyber attacks that could target them. These can be structured, for example, as threat actor profiles, country profiles, malware or tools analyses, or cyber trend studies.
Member Organizations, based on the intelligence produced, should be able to perform tailored threat assessments to define the relevancy and level of potential threats, as well as the probability of attacks.
The CISO is responsible for validating the quality and relevance of the information. This information can be of particular interest to senior and executive management, business owners, owners of information assets, etc. This information is particularly valuable for instance when defining business strategies, planning security interventions, or following significant cyber incidents in the sector or in the country.
Domain 3: Operational Cyber Threat Intelligence
Operational CTI helps the Member Organizations to understand the nature, intent, and timing of a specific attack, and provides insight into the behavior of a threat actor on a network.
Operational CTI provides detailed information on the behavior and modus operandi of threat actors used to carry out cyber attacks. Generally, this information is commonly taxonomized in Tactics, Techniques, and Procedures (TTPs).
Principle 15: Define the Attack Chain
Member Organizations should define and taxonomize the various phases of an attack performed by the threat actors based on industrial standards or frameworks (e.g. kill chain, unified kill chain, etc.). Moreover, Member Organizations should analyze information and modus operandi of the threat actors based on a structured approach to attacks (e.g. MITRE framework adopts a modified version of the unified kill-chain).
Principle 16: Identify TTPs
Member Organizations should analyze the information collected from sources related to relevant threat actors, tools, or malware to identify relevant Techniques, Tactics, and Procedures (TTPs). In addition, Member Organizations should adopt a taxonomy of attacks and classification of such TTPs (e.g. MITRE ATT&CK). Based on the defined taxonomy, they should build threat actor behavior profiles and identify techniques used by threat actors. Member Organizations should rely also on Indicators of Compromise (loCs) for the identification of these TTPs.
Principle 17: Identify Malware and Tools
Member Organizations should identify malware and tools during an attack, as well as conduct a general classification of these to use at an organizational level (e.g. Banking Trojan, Ransomware, etc.). Member Organizations can obtain information regarding the different types of malware and tools used by the threat actors using different sources, such as Indicators of Compromises (loCs), dark web, deep web, OSINT, code repositories, information sharing platforms, etc.
Domain 4: Technical and Tactical Cyber Threat Intelligence
Technical and tactical threat intelligence provide technical information regarding specific attacks performed by threat actors such as loCs, Yara Rules, etc.
The indicators of technical threat intelligence are collected from active and past campaigns obtained from public sources, technical indicators collected within the organization, and/or data feeds provided by external third-parties.
Principle 18: Collect IoCs
Member Organizations should identify, collect, and aggregate loCs and implement them in their defence infrastructure. Member Organizations should be able to collect details on specific implementation of malware and tools in order to understand how the organization is likely to be attacked and determine whether appropriate detection and mitigation mechanisms exist or whether they need to be implemented. In addition, Member Organizations should take into consideration different threat intelligence platforms and sources to obtain such technical information.
Principle 19: Monitor and Report Vulnerabilities
Member Organizations should constantly monitor announcements of new vulnerabilities discovered, as well as zero-day vulnerabilities exploited by threat actors. They should report these vulnerabilities to relevant parties within the organization (e.g. those in charge of patching management). These communications should be done in accordance to Member Organizations' internal procedures (e.g. SLA and KPI).
Member Organization should adapt a risk-based approach that correlates asset value, the severity of vulnerabilities, and threat actor activity via the use of threat intelligence and analytics to calculate realistic risk rating. This rating should be used to prioritize remediation activities. In addition, Member Organization should use a risk-based approach to employ mitigating controls, such as intrusion prevention system (IPS), when unable to patch vulnerabilities to reduce the attack surface and prevent vulnerabilities from being exploited.

