Appendices
Appendix A – Defined Terms
The following are considered defined terms for the purpose of this Framework.
Defined Term Definition Access Management The process of granting authorised users the right to use
a service, while preventing access to non-authorised
users.Anomalous Session Log-in sessions to mobile or online services that have
different log-in parameters to those previously used by
the customer, e.g., Device ID or location; or when the IP
address is flagged as a risk.Anomaly Detection Finding patterns in data that depart significantly from the
expected behaviour. Fraud anomaly detection can be
implemented as an intelligence tool using unsupervised
Machine Learning algorithms.Artificial Intelligence The use of computer systems to perform tasks typically
requiring human knowledge and logical capabilities,
often in problem solving scenarios.Black Box System A complex system where the internal rules and
mechanisms are not visible to or understood by the
system owner.Blacklist A list of untrustworthy or high risk individuals or entities
that should be excluded and avoided. Also known as
block-list.Case Management System A system used to manage alerts and fraud incidents from
an initial report, through investigation, resolution and
remediation where required.Code of Conduct A defined set of expectations which outline principles,
values, and behaviours that an organisation considers
important to its operations and success.Contractor An individual or organisation under contract for the
provision of services to an organisation.Counter-Fraud Culture The shared values, beliefs, knowledge, attitudes and
understanding about fraud risk within an organisation. In
a strong Counter-Fraud culture people proactively
identify, discuss, and take responsibility for fraud risks.Counter-Fraud
GovernanceA set of responsibilities and practices exercised by the
Board, Executive and Senior Management with the goal
of providing strategic direction for countering fraud,
ensuring that Counter-Fraud objectives are achieved, ascertaining that fraud risks are managed appropriately
and verifying that the enterprise's resources are used
responsibly.Counter-Fraud
Governance Committee
(CFGC)An established group of individuals tasked with providing
oversight and direction, and ensuring that the
organisation’s combined Counter-Fraud capabilities are
functioning appropriately and efficiently.Counter-Fraud Maturity The extent to which an organisation’s resources are
effectively implemented for the purpose of countering
fraud in comparison to global accepted standards and
best practice.Counter-Fraud Policy A set of criteria for the provision of Counter-Fraud
activities. It sets the commitment and objectives for
Counter-Fraud and documents responsibilities.Counter-Fraud
ProgrammeA collection of policies, processes, guidelines, risk
management approaches, actions, training, best
practices, assurance, and technologies that are used to
protect the Member Organisation and its customers
against internal and external fraud threats.Counter-Fraud Strategy A high-level plan, consisting of projects and initiatives, to
mitigate fraud risks while complying with legal, statutory,
contractual, and internally prescribed requirements.Counter-Fraud
DepartmentA dedicated department or team established for the
purpose of managing the implementation of the
organisation’s Counter-Fraud objectives.Critical services Services provided by a third party where a failure or
disruption in the provision of services could leave the
Member Organisation unable to serve its customers or
meet its regulatory obligations.Cyber Security Cyber security is defined as the collection of tools,
policies, security concepts, security safeguards,
guidelines, risk management approaches, actions,
training, best practices, assurance, and technologies that
can be used to protect the Member Organisation's
information assets against internal and external threats.Due Diligence The investigation of an employee, customer or third
party to confirm facts and that it is as presented.Emergency Stop A self-service capability for customers to immediately
freeze their account and block further transactions if they
suspect their account has been compromisedEmployee Employees encompass members of the Board of
Directors and its committees, Executives, permanent and
contract employees, consultants, and employees working
through a third partyEntity Resolution A process to identify data records in a single data source
or across multiple data sources that refer to the same
real-world entity and to link the records together.External Fraud A fraudulent event conducted by any persons on the
‘outside’ of the organisation i.e., not employed by the
organisation.Financial Crime Criminal activities to provide economic benefit including
money laundering; terrorist financing; bribery and
corruption; and market abuse and insider dealing.Fraud Any act that aims to obtain an unlawful benefit or cause
loss to another party. This can be caused by exploiting
technical or documentary means, relationships or social
means, using functional powers, or deliberately
neglecting or exploiting weaknesses in systems or
standards, directly or indirectly.Fraud case An individual occurrence of fraud recognised by an
organisation.Fraud Landscape/Threat
LandscapeFraud threats, trends, and developments in the political,
economic, social, technological, or legal environment.Fraud Response Plan A plan which details the actions to be undertaken when a
fraud is suspected or has been detected. This will include
reporting protocols, team responsibilities and
information logging.Fraud Risk Appetite The level of fraud risk that an organisation is willing to
accept or tolerate in pursuit of its objectives.Fraud Risk Assessment A process aimed at addressing the organisation’s
vulnerability to fraud. This will include identification of
fraud risks, assessment of the likelihood that fraud risks
will occur and the resulting impact, determination of the
appropriate response, and review of the control
framework.Fraud Risk Management The ongoing process of identifying, analysing, monitoring,
and responding to fraud risks to which the organisation
and its customers are exposed.Fraud Scenario Analysis The testing of devised fraud scenarios for the purpose of
assessing the current capability of fraud systems within
the organisation.Fraud Threat Any circumstance or event with the potential to result in
a fraud event occurring.Fraud Typology A categorisation of a fraud event based on its
methodology and common themes with other fraud
events.Geofencing Restricting access to online or mobile services based
upon the user's geographical location.Incident A fraud case or series of associated cases. Inherent Risk The fraud risks posed to the organisation’s business
operations or its customers if there were no controls
present.Intelligence Monitoring The process of continually reviewing and gathering
intelligence on new and emerging fraud threats and
typologies from a comprehensive range of sources.Internal Fraud Fraud committed by or with the assistance of people
employed by the organisation.Key Risk Indicators (KRIs) A measure used to indicate the probability an activity or
organisation will exceed its defined risk appetite. KRIs are
used by organisations to provide an early signal of
increasing risk exposures in various areas of the
enterprise.Keyword Analysis Codifying rules to match key words on a look-up table to
those within key fields of a fraud case record. Complexity
can be added to rules such as requiring the words to be
in a particular order or high-risk terms that have often
indicated fraud.Machine Learning The use of computer systems that have the capability to
learn and adapt without explicit instruction through the
use of algorithms or models to analyse and build on
patterns and trends in data.Management Information Information collated and then presented, often in the
form of a report or statement, to management or
decision makers for the purpose of identifying trends,
solving issues and/or forecasting the future.Member Organisation All financial institutions or financial services providers
regulated by SAMA.Model Validation Analysis to assess whether the outputs of a system are
performing as expected.Mule accounts Accounts set-up (often via remote or online channels) to
receive fraudulently obtained funds and launder the
proceeds of crime.Multi-Factor
AuthenticationAuthentication using two or more factors to achieve
authentication. Factors include something you know
(e.g., password/PIN), something you have (e.g.,
cryptographic identification device, token), or something
you are (e.g., biometric).Near Misses Potential fraud incidents that are detected and
remediated prior to the fraud incident resulting in a
monetary loss.Policy Breach The failure to comply with or disregard of policy
requirements.Precision and Recall
TestingMetrics to evaluate the effectiveness of models.
Precision: The ability of a classification model to identify
only the relevant data points.
Recall: The ability of a model to find all the relevant cases
within a data set.Predictive Analytics The use of statistics and modelling techniques to
determine future outcomes or performance.RACI Matrix Illustrates who is Responsible, Accountable, Consulted
and Informed within an organisational framework.Residual Risk The remaining risk after management has implemented a
risk response.Risk A measure of the extent to which an organisation is
threatened by a potential circumstance or event, and
typically a function of: (i) the adverse impacts that would
arise if the circumstance or event occurs; and (ii) the
likelihood of occurrence.Risk Factors Different categories of risk that organisations must
consider considered when performing a Fraud Risk
AssessmentRules Rules used in fraud prevention and detection systems use
correlation, statistics, and logical comparison of data to
identify a pattern based on insights gained from previous
known fraud incidents.Scams Where an individual is tricked into making or authorising
a payment to a criminal’s account. Scammers typically
use social engineering and can impersonate banks,
investment opportunities, utility companies and
government bodies using emails, phone calls and SMS
that appear genuine.Sectorial Anti-Fraud
CommitteeA committee governed by SAMA to combat fraud
involving Member Organisations operating in the
Kingdom (e.g., Banking Anti-Fraud Committee).Senior Management The highest level of management in an organisation (the
level below the Board) and their direct reports.Service Level Agreement
(SLA)The specific responsibilities for delivery, typically an
agreement on timeliness or quality, for example relating
to management of fraud alerts.Static Data Data with low change frequency (e.g., name, email
address, mobile phone number, signatory rights,
specimen signatures, power-of-attorney).The Cyber Security
FrameworkSAMA's Cyber Security Framework. Third Party A separate unrelated entity that provides an organisation
with a service. This may include suppliers, technology
providers (e.g., Absher, Nafath), outsourcers,
intermediaries, brokers, introducers, and agents.Threat Intelligence Threat intelligence is evidence-based knowledge,
including context, mechanisms, indicators, implications,
and actionable advice, about an existing or emerging
menace or hazard to assets that can be used to inform
decisions regarding the subject's response to that
menace or hazard.Trend Analysis The process of collecting and reviewing information to
identify patterns and predict future trends.Trusted Device A trusted device is a device that the customer owns,
controls access to, and uses often.Violation Any act, or concealment of acts, of fraud, corruption,
collusion, coercion, unlawful conduct, misconduct,
financial mismanagement, accounting irregularities,
conflict of interest, wrongful conduct, illegal or unethical
practices or other violations of any applicable laws and
instructions.Whistle Blowing Policy SAMA Whistle Blowing Policy for Financial
Institutions.Wholesale Payment
Endpoint SecurityMeasures taken with respect to endpoint hardware,
software, physical access, logical access, organisation and
processes at a point in place and time at which payment
instruction information is exchanged between two
parties in the ecosystem.Appendix B – Fraud Types that May Impact a Member Organisation and Its Customers.
The following is a non-exhaustive list of fraud types that should be considered by a Member Organisation when relevant to its products.
- Social engineering (e.g., capture of customer credentials; investment scams; purchase scams; invoice scams; advance fee scams).
- Account takeover (e.g., gaining access to a customer product or device to control assets or transact).
- Impersonation (e.g., obtaining personal information to use for own benefit; assuming the identity of another to access products; impersonating a government body to obtain customer information).
- Internal fraud (e.g., misappropriation of assets; procurement fraud; theft of assets or cash; theft of intellectual property; falsification of information; unauthorised passing of information to third parties; false expense claims; abuse of authority; collusion; use of organisation assets for own gain; diversion of funds).
- Accounting fraud (e.g., concealment; false invoicing; payroll fraud; improper revenue recognition; overstatement of assets; understatement of liabilities; customer overbilling; treasury and investment fraud).
- Application fraud (e.g., failing to disclose information; falsification of information; providing false documents).
- Wholesale Payment Endpoint Security fraud.
- Banking and payment products: Credit/Debit card fraud; Online or mobile app payment fraud; Cheque fraud; ATM fraud; Mule fraud.
- Credit and lending products: Mortgage fraud; Loan fraud.
Appendix C – How to Request an Update to the Framework
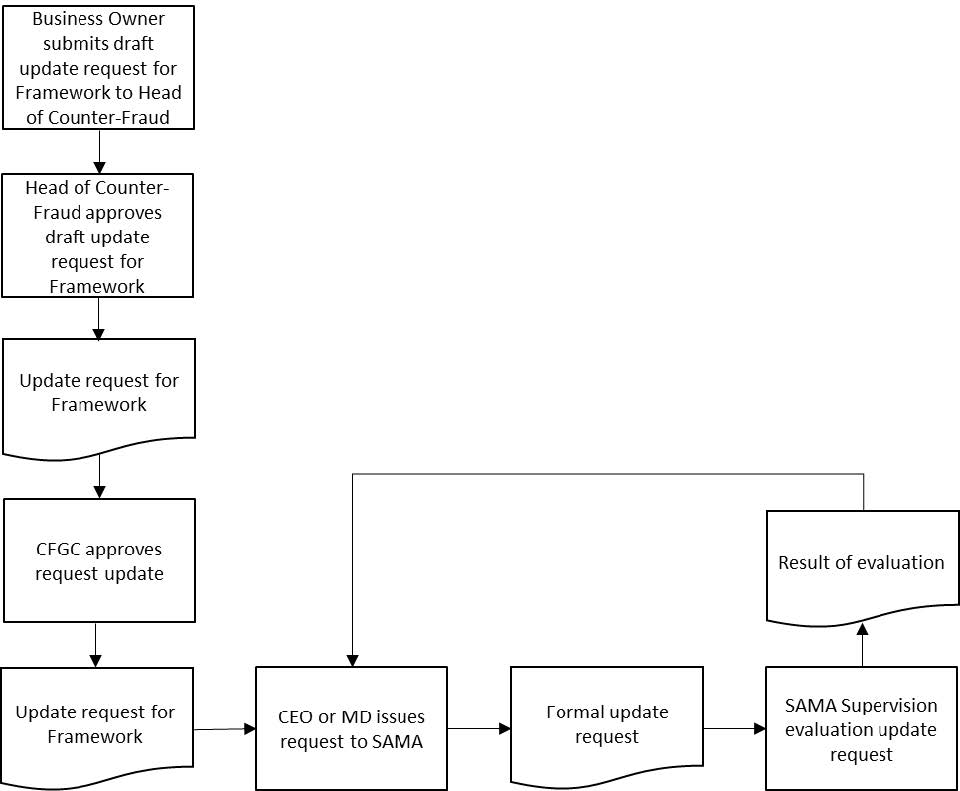
- Below is an illustration of the process for requesting an update to the Framework.
- Detail information supported by pros and cons about the suggested update.
- The request should first be approved by the Head of Counter-Fraud before submitting to the Counter-Fraud Governance Committee (CFGC).
- The request should be approved by Member Organisation's CFGC.
- The request should be sent formally in writing to the manager 'General Department of Cyber Risk Control' via the Member Organisation's CEO or managing director.
- 'General Department of Cyber Risk Control' will evaluate the request and inform the Member Organization.
- The current Framework remains applicable while the requested update is being considered, processed and if applicable is approved and processed.
Appendix D – Framework Update Request Form
Request to Update the Counter-Fraud Framework
A submission to the manager of SAMA General Department of Cyber Risk Control.
SAMA will consider requests from a member organisation (MO) to update its Counter-Fraud Framework based on the information submitted using the form below. A separate form must be completed for each requested update. Please note that all required fields must be properly filled in before SAMA will begin the review process
Requestor Information
REQUESTOR'S SIGNATURE*
xREQUESTOR'S POSITION* DATE* REQUESTOR'S NAME*
MEMBER ORGANISATION OF REQUESTOR*
FRAMEWORK SECTION*:
PURPOSE OF REQUESTED UPDATE (including detailed information on its pros and cons)*:
PROPOSAL*:
Approvals
1. MO’s HEAD OF COUNTER-FRAUD APPROVAL*
DATE*
2. MO’S COUNTER-FRAUD GOVERNANCE COMMITTEE
APPROVAL*
APPROVER’S POSITION*
DATE*
3. SAMA DECISION
SAMA APPROVAL
DATE
* Denotes required fields
Appendix E – How to Request a Waiver from the Framework
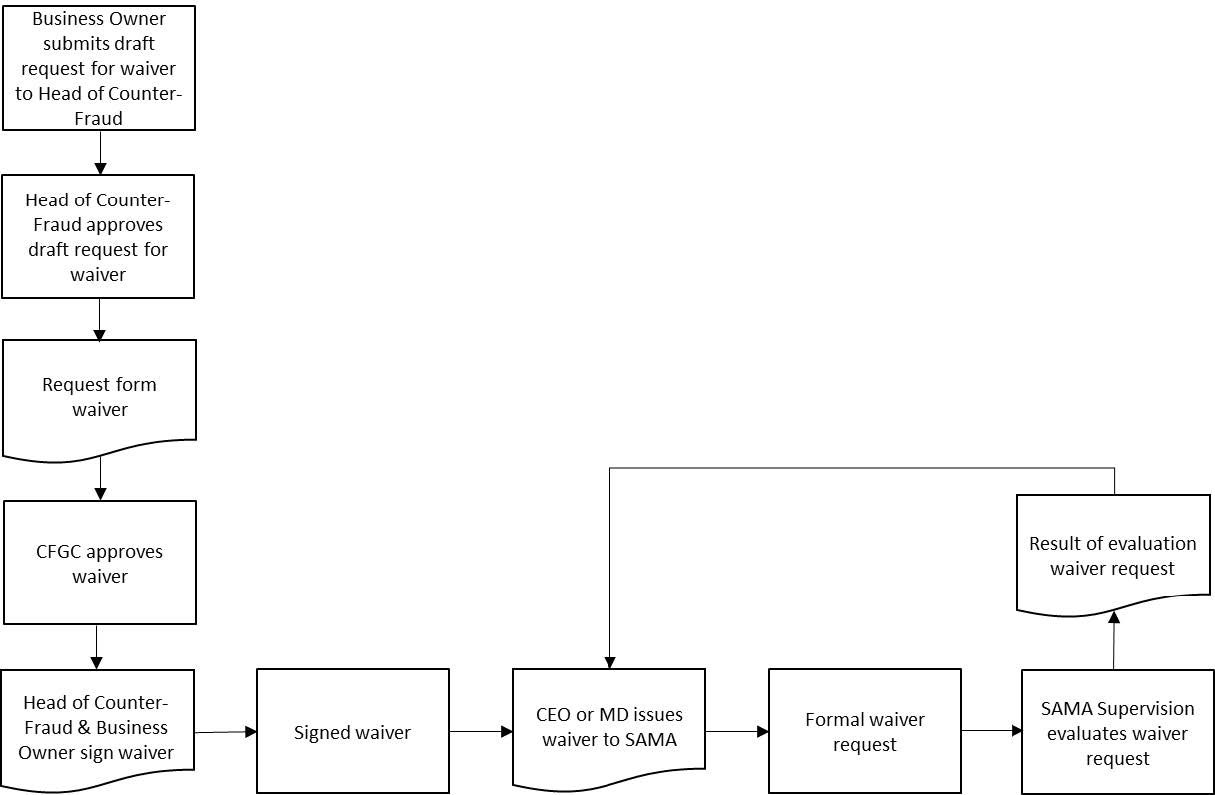
Below is an illustration of the process for requesting a waiver from the Framework.
- Detail description about the reasons that the member organisation could not meet the required control.
- Detail description about the available or suggested compensating controls.
- The waiver request should first be approved by the Head of Counter-Fraud before submitting to the Counter-Fraud Governance Committee (CFGC).
- The waiver request should be approved by the members of Member Organisation’s Counter-Fraud Governance Committee.
- The waiver request should be signed by the Head of Counter-Fraud and relevant (business) owner.
- The waiver request should be formally issued in writing to the manager of ‘General Department of Cyber Risk Control’ via the Member Organisation’s CEO or managing director.
- ‘General Department of Cyber Risk Control’ will evaluate the waiver request and inform the Member Organisation.
The current Framework remains applicable while the requested waiver is being evaluated and processed, until the moment of granting the waiver.
Appendix F – Framework Waiver Request Form
Request for Waiver from the SAMA Counter-Fraud Framework
A submission to the manager of 'General Department of Cyber Risk Control’
SAMA will consider requests for waiver from a member organisation (MO) from its Counter-Fraud Framework based on the information submitted using the form below. A separate form must be completed for each requested waiver. Please note that all required fields must be properly filled in before SAMA will begin the review process.
Requestor Information
REQUESTOR'S SIGNATURE*
xREQUESTOR'S POSITION* DATE* REQUESTOR'S NAME*
MEMBER ORGANISATION OF REQUESTOR*
FRAMEWORK CONTROL*:
DETAILED DESCRIPTION OF WHY CONTROL CANNOT BE IMPLEMENTED*:
DETAILED DESCRIPTION OF AVAILABLE OR SUGGESTED COMPENSATING CONTROLS*:
Approvals
1. MO’s HEAD OF COUNTER-FRAUD APPROVAL*
DATE*
2. MO’S COUNTER-FRAUD GOVERNANCE COMMITTEE
APPROVAL*
APPROVER’S POSITION*
DATE*
3.SAMA DECISION
SAMA APPROVAL
DATE**
* Denotes required fields
** The validity of this waiver is one year. It is the Member Organisations responsibility to ensure renewal of this waiver.
Appendix G – Supervisor Notification Form
Fraud Supervisory Notification
A submission to the manager of SAMA General Department of Cyber Risk Control.
SAMA requires immediate notification of new fraud typologies and significant fraud incidents to mitigate the risk of the fraud impacting additional customers, other organisations, or the financial sector in the KSA. This form should be used to provide the notification. Please note that all required information must be provided, however it is understood that not all information may be available at the time of notification. Where information is not available at the time of notification, any gaps should be supplied to SAMA promptly as the investigation progresses.
Notifier Information
NOTIFIER’S SIGNATURE*
NOTIFIER’S POSITION*
DATE*
NOTIFIER’S NAME*
MEMBER ORGANISATION OF NOTIFIER*
FRAUD NOTIFICATION TYPE*
DATE OF INCIDENT*
☐ New typology ☐ Significant internal fraud ☐ Significant external fraud ☐ Significant accounting irregularity ☐ Wholesale Payment Endpoint Security Fraud ORIGIN OF THE INCIDENT*:
METHODS USED*:
RELATED PARTIES (INTERNAL AND EXTERNAL)*:
OUTCOME (INCLUDING LOSSES WHERE APPLICABLE)*:
CORRECTIVE ACTIONS*:
ADDITIONAL INFORMATION:
* Denotes required fields

