2 Framework Structure and Features
2.1 Structure
The Framework is structured around four main domains, namely:
- Cyber Security Leadership and Governance.
- Cyber Security Risk Management and Compliance.
- Cyber Security Operations and Technology.
- Third Party Cyber Security.
For each domain, several subdomains are defined. A subdomain focusses on a specific cyber security topic. Per subdomain, the Framework states a principle, objective and control considerations.
- A principle summarizes the main set of required cyber security controls related to the subdomain.
- The objective describes the purpose of the principle and what the set of required cyber security controls are expected to achieve.
- The control considerations reflects the mandated cyber security controls that should be considered.
Control considerations have been uniquely numbered throughout the Framework. Where applicable, a control consideration can consist of up to 4 levels.
The control considerations are numbered according to the following numbering system:
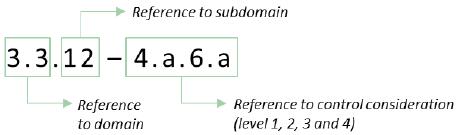
Figure 1 - Control consideration numbering system
The figure below illustrates the overall structure of the Framework and indicates the cyber security domains and subdomains, including a reference to the applicable section of the Framework.
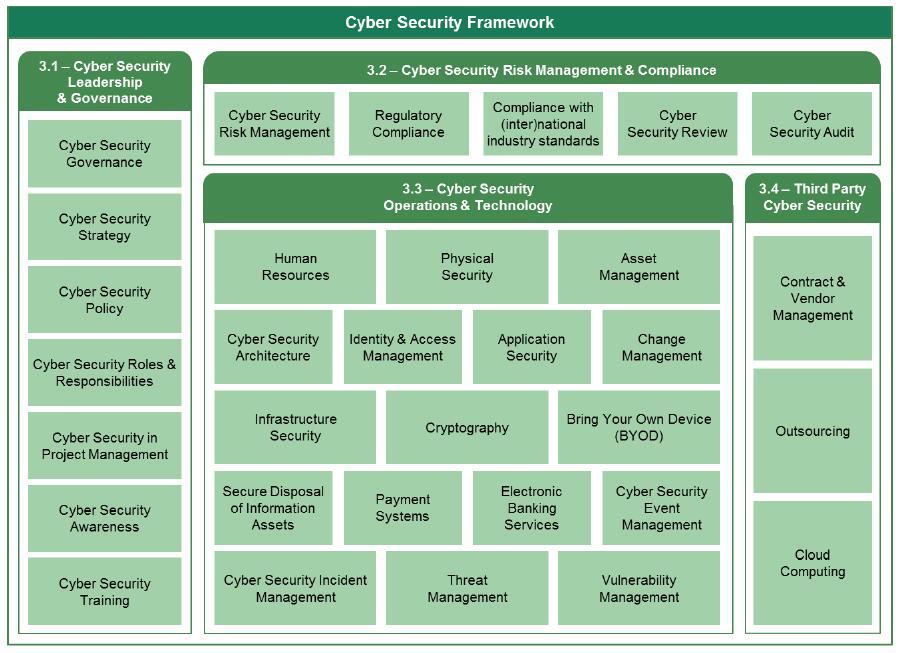
Figure 2 - Cyber Security Framework2.2 Principle-Based
The Framework is principle based, also referred to as risk based. This means that it prescribes key cyber security principles and objectives to be embedded and achieved by the Member Organization. The list of mandated control considerations provides additional direction and should be considered by the Member Organization in achieving the objectives. When a certain control consideration cannot be tailored or implemented, the Member Organization should consider applying compensating controls, pursuing an internal risk acceptance and requesting a formal waiver from SAMA.
Please refer to Appendix D for details for the - How to request a Waiver from the Framework - process.
2.3 Self-Assessment, Review and Audit
The implementation of the Framework at the Member Organization will be subject to a periodic self-assessment. The self-assessment will be performed by the Member Organization based on a questionnaire. The self-assessments will be reviewed and audited by SAMA to determine the level of compliance with the Framework and the cyber security maturity level of the Member Organization.
Please refer to ’2.4 Cyber Security Maturity Model’ for more details about the cyber security maturity model.
2.4 Cyber Security Maturity Model
The cyber security maturity level will be measured with the help of a predefined cyber security maturity model. The cyber security maturity model distinguishes 6 maturity levels (0, 1, 2, 3, 4 and 5), which are summarized in the table below. In order to achieve levels 3, 4 or 5, a Member Organization must first meet all criteria of the preceding maturity levels.
Maturity Level Definition and Criteria Explanation 0
Non-existent
- No documentation.
- There is no awareness or attention for certain cyber security control.
- Cyber security controls are not in place. There may be no awareness of the particular risk area or no current plans to implement such cyber security controls.
1
Ad-hoc
- Cyber security controls is not or partially defined.
- Cyber security controls are performed in an inconsistent way.
- Cyber security controls are not fully defined.
- Cyber security control design and execution varies by department or owner.
- Cyber security control design may only partially mitigate the identified risk and execution may be inconsistent.
2
Repeatable but informal
- The execution of the cyber security control is
- based on an informal and unwritten, though standardized, practice.
- Repeatable cyber security controls are in place. However, the control objectives and design are not formally defined or approved.
- There is limited consideration for a structured review or testing of a control.
3
Structured and formalized
- Cyber security controls are defined, approved and implemented in a structured and formalized way.
- The implementation of cyber security controls can be demonstrated.
- Cyber security policies, standards and procedures are established.
- Compliance with cyber security documentation i.e., policies, standards and procedures is monitored, preferably using a governance, risk and compliance tool (GRC).
- key performance indicators are defined, monitored and reported to evaluate the implementation.
4
Managed and measurable
- The effectiveness of the cyber security controls are periodically assessed and improved when necessary.
- This periodic measurement, evaluations and opportunities for improvement are documented.
- Effectiveness of cyber security controls are measured and periodically evaluated.
- key risk indicators and trend reporting are used to determine the effectiveness of the cyber security controls.
- Results of measurement and evaluation are used to identify opportunities for improvement of the cyber security controls.
5
Adaptive
- Cyber security controls are subject to a continuous improvement plan.
- The enterprise-wide cyber security program focuses on continuous compliance, effectiveness and improvement of the cyber security controls.
- Cyber security controls are integrated with enterprise risk management framework and practices.
- Performance of cyber security controls are evaluated using peer and sector data.
Table 1 - Cyber Security Maturity Model
The objective of the Framework is to create an effective approach for addressing cyber security and managing cyber security risks within the Financial Sector. To achieve an appropriate cyber security maturity level, the Member Organizations should at least operate at maturity level 3 or higher as explained below.
2.4.1 Maturity Level 3
To achieve level 3 maturity, a Member Organization should define, approve and implement cyber security controls. In addition, it should monitor compliance with the cyber security documentation .
The cyber security documentation should clearly indicate “why”, “what” and “how” cyber security controls should be implemented. The cyber security documentation consists of cyber security policies, cyber security standards and cyber security procedures.
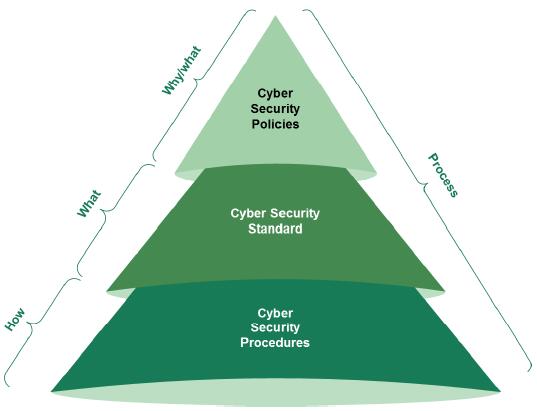
Figure 3 - Cyber Security Documentation Pyramid
The cyber security policy should be endorsed and mandated by the board of the Member Organization and stating “why” cyber security is important to the Member Organization. The policy should highlight which information assets must be protected and “what” cyber security principles and objectives should be established.
Based on the cyber security policy, cyber security standards must be developed. These standards define “what“ cyber security controls must be implemented, such as security and system parameters, segregation of duties, password rules, monitoring events and back-up and recovery rules. The standards support and reinforce the cyber security policy and are to be considered as cyber security baselines.
The step-by-step tasks and activities that should be performed by staff, third parties or customers of the Member Organization are detailed in the cyber security procedures. These procedures prescribe “how” the cyber security controls, tasks and activities have to be executed in the operating environment and support the safeguarding of the information assets of the Member Organization according to the cyber security policy and standards.
The process in the context of this framework is defined as a structured set of activities designed to accomplish the specified objective. A process may include policies, standards, guidelines, procedures, activities and work instructions, as well as any of the roles, responsibilities, tools and management controls required to reliably deliver the output.
The actual progress of the implementation, performance and compliance of the cyber security controls should be periodically monitored and evaluated using key performance indicators (KPIs).
2.4.2 Maturity Level 4
To achieve maturity level 4, the Member Organization should periodically measure and evaluate the effectiveness of implemented cyber security controls. In order to measure and evaluate whether the cyber security controls are effective, key risk indicators (KRIs) should be defined. A KRI indicates the norm for effectiveness measurement and should define thresholds to determine whether the actual result of measurement is below, on, or above the targeted norm. KRIs are used for trend reporting and identification of potential improvements.
2.4.3 Maturity Level 5
Maturity level 5 focuses on the continuous improvement of cyber security controls. Continuous improvement is achieved through continuously analyzing the goals and achievements of cyber security and identifying structural improvements. Cyber security controls should be integrated with enterprise risk management practices and supported with automated real-time monitoring. Business process owners should be accountable for monitoring the compliance of the cyber security controls, measuring the effectiveness of the cyber security controls and incorporating the cyber security controls within the enterprise risk management framework . Additionally, the performance of cyber security controls should be evaluated using peer and sector data.

